Cloudy with a Chance of Cyberattacks: Dangling Resources Abuse on Cloud Platforms (2403.19368v1)
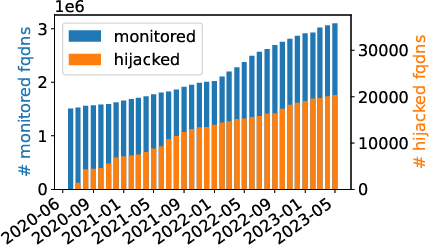
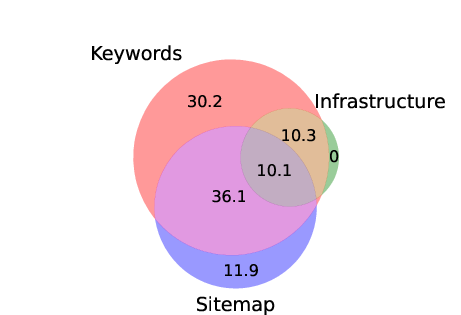
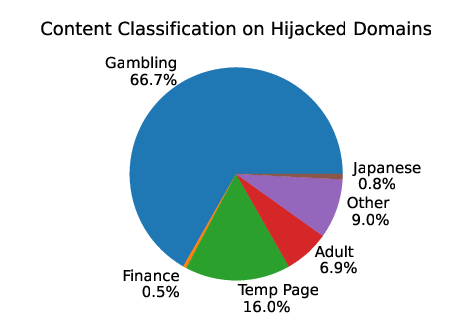
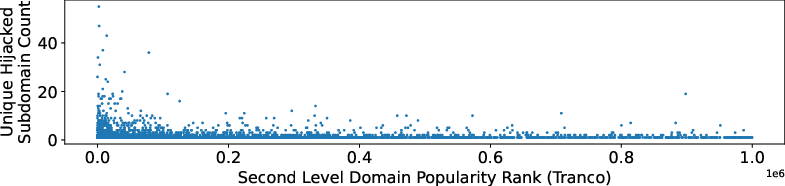
Abstract: Recent works showed that it is feasible to hijack resources on cloud platforms. In such hijacks, attackers can take over released resources that belong to legitimate organizations. It was proposed that adversaries could abuse these resources to carry out attacks against customers of the hijacked services, e.g., through malware distribution. However, to date, no research has confirmed the existence of these attacks. We identify, for the first time, real-life hijacks of cloud resources. This yields a number of surprising and important insights. First, contrary to previous assumption that attackers primarily target IP addresses, our findings reveal that the type of resource is not the main consideration in a hijack. Attackers focus on hijacking records that allow them to determine the resource by entering freetext. The costs and overhead of hijacking such records are much lower than those of hijacking IP addresses, which are randomly selected from a large pool. Second, identifying hijacks poses a substantial challenge. Monitoring resource changes, e.g., changes in content, is insufficient, since such changes could also be legitimate. Retrospective analysis of digital assets to identify hijacks is also arduous due to the immense volume of data involved and the absence of indicators to search for. To address this challenge, we develop a novel approach that involves analyzing data from diverse sources to effectively differentiate between malicious and legitimate modifications. Our analysis has revealed 20,904 instances of hijacked resources on popular cloud platforms. While some hijacks are short-lived (up to 15 days), 1/3 persist for more than 65 days. We study how attackers abuse the hijacked resources and find that, in contrast to the threats considered in previous work, the majority of the abuse (75%) is blackhat search engine optimization.
- Zombie awakening: Stealthy hijacking of active domains through dns hosting referral. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, pages 1307–1322, 2020.
- The circle of life: A large-scale study of the iot malware lifecycle. In USENIX Security Symposium, pages 3505–3522, 2021.
- Cloud strife: Mitigating the security risks of domain-validated certificates. In Internet Society Symposium on Network and Distributed System Security (NDSS), 2018.
- Study on Domain Name System (DNS) abuse. Publications Office of the European Union, 2022.
- A large-scale analysis of the security of embedded firmwares. In 23rd USENIX Security Symposium (USENIX Security 14), pages 95–110, 2014.
- An internet-wide view of internet-wide scanning. In 23rd USENIX Security Symposium (USENIX Security 14), pages 65–78, 2014.
- Zmap: Fast internet-wide scanning and its security applications. In Usenix Security, volume 2013, 2013.
- Lzr: Identifying unexpected internet services. In USENIX Security Symposium, pages 3111–3128, 2021.
- Security analysis on practices of certificate authorities in the https phishing ecosystem. ASIA CCS ’21: Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security, pages 407–420, May 2021.
- All things considered: an analysis of iot devices on home networks. In Proceedings of the 28th USENIX Conference on Security Symposium, pages 1169–1185, 2019.
- Tranco: A research-oriented top sites ranking hardened against manipulation. In Proceedings of the 26th Annual Network and Distributed System Security Symposium, NDSS 2019, February 2019.
- All your dns records point to us: Understanding the security threats of dangling dns records. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pages 1414–1425, 2016.
- Cloudy with a chance of breach: Forecasting cyber security incidents. In 24th USENIX security symposium (USENIX Security 15), pages 1009–1024, 2015.
- Ethical considerations in network measurement papers. Communications of the ACM, 59(10):58–64, 2016.
- Tranco: A research-oriented top sites ranking hardened against manipulation. arXiv preprint arXiv:1806.01156, 2018.
- Can i take your subdomain? exploring same-site attacks in the modern web. In USENIX Security Symposium, pages 2917–2934, 2021.
- Towards a complete view of the certificate ecosystem. In Proceedings of the 2016 Internet Measurement Conference, pages 543–549, 2016.
- Detecting and measuring security risks of hosting-based dangling domains. Proceedings of the ACM on Measurement and Analysis of Computing Systems, 7(1):1–28, 2023.
Sponsor
Paper Prompts
Sign up for free to create and run prompts on this paper using GPT-5.
Top Community Prompts
Collections
Sign up for free to add this paper to one or more collections.