- The paper introduces AIIPot which leverages transformer-based models and reinforcement learning to dynamically interact with attackers in IoT environments.
- Its honey-chatbot uses a fine-tuned BERT model and a Markov Decision Process to simulate realistic device behavior, extending session lengths and capturing a diverse range of exploits.
- Evaluation results showed AIIPot engaged 987 IP addresses over 20 days and captured 6,235 distinct requests, demonstrating its enhanced ability to collect rich attacker data.
AIIPot: Adaptive Intelligent-Interaction Honeypot for IoT Devices
Introduction
The proliferation of IoT devices presents substantial security challenges due to their connectivity and inherent vulnerabilities, such as weak-password protections and vendor-dependent security flaws. Traditional IoT defense mechanisms, such as honeypots, have limitations due to their static interactions and high maintenance costs when dealing with the vast heterogeneity of IoT devices. This paper introduces AIIPot, an intelligent-interaction honeypot leveraging machine learning, specifically transformer models and reinforcement learning, to dynamically interact with attackers, capturing exploits effectively through adaptive engagement.
AIIPot Framework
AIIPot consists of three primary components: the honey-chatbot, req/res database, and request evaluator. The core innovation lies within the honey-chatbot, which employs a transformer-based architecture (BERT) and a Markov Decision Process (MDP) to predict and optimize response strategies. It's designed to emulate intelligent device behavior by adapting its interactions based on attacker engagement, thereby increasing the likelihood of eliciting substantial exploit attempts.
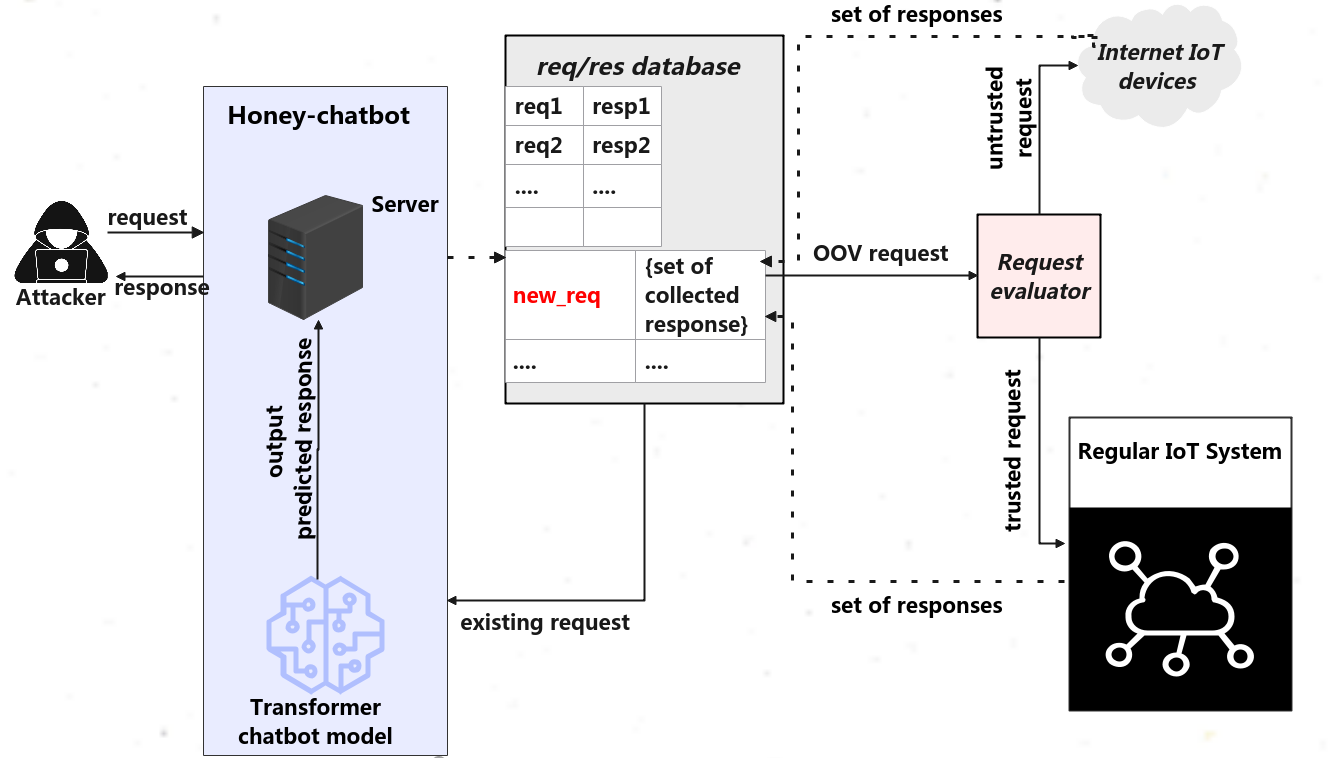
Figure 1: High-level overview of AIIPot, showing its components and interaction flow.
The honey-chatbot dynamically determines the most expected response to an attacker's request via a BERT model, pre-trained on a dataset of potential interactions. Subsequently, an MDP leverages these predictions to model the potential future conversation with the attacker, using a reward-based system to incentivize prolonged interactions that may culminate in revealing exploit tactics.
The BERT model is fine-tuned to distinguish valid responses to incoming requests, supporting diverse IoT dialogue simulations. The MDP further refines interactions by quantifying state transitions based on past engagements, optimizing responses to align with attacker expectations.
Req/Res Database and Request Evaluation
The req/res database facilitates AIIPot's adaptability, cataloguing request-response pairs to enable swift response generation. Unrecognized requests are processed through a request evaluator, using an SVM classifier to distinguish between benign and untrusted requests. This ensures that only safe interactions contribute to the learning database, continuously enriching AIIPot’s capability to simulate realistic IoT environments.
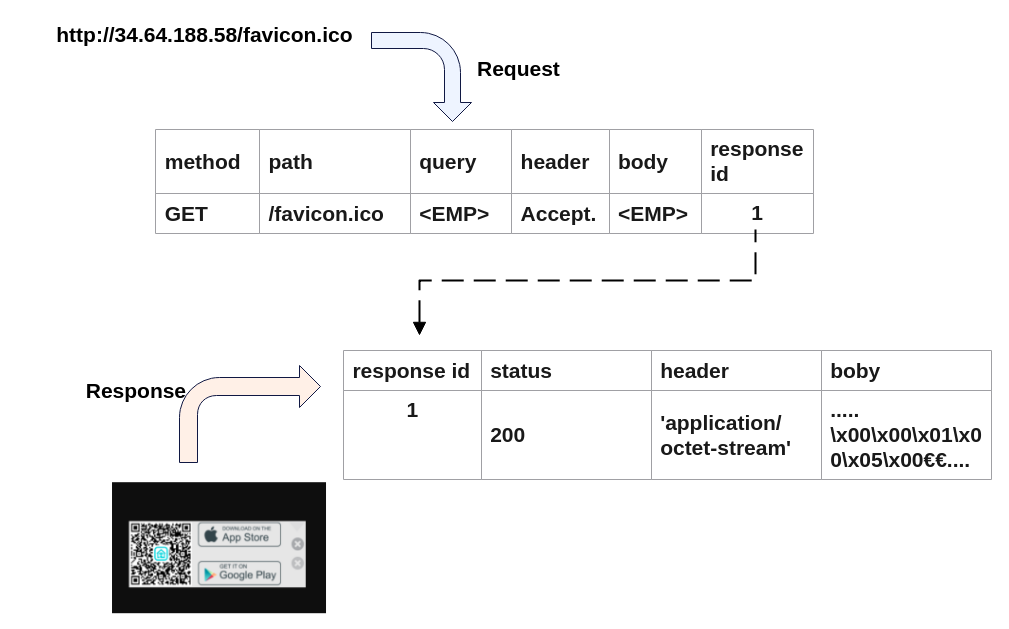
Figure 2: Req/res database entries, illustrating how request-response pairs are stored for reference.
Evaluation and Results
AIIPot was evaluated based on session interaction lengths, information volume exchanged, and captured exploit variety, juxtaposed against existing honeypot solutions. The results demonstrated AIIPot's superior ability to sustain interactions, reflected in a 987 IP-address engagement over 20 days, capturing 6,235 distinct requests. Notably, AIIPot significantly extended interaction lengths, thereby increasing the likelihood of capturing complex exploit attempts.
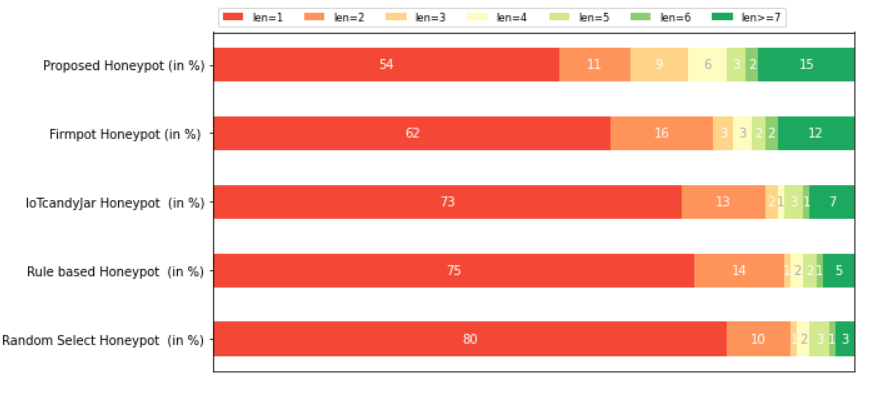
Figure 3: Session length comparison with attackers between honeypots, indicating AIIPot’s enhanced deception performance.
The volume of information collected per session also heightened, indicating richer data acquisition from attackers, pivotal for understanding and defending against evolving IoT threats.
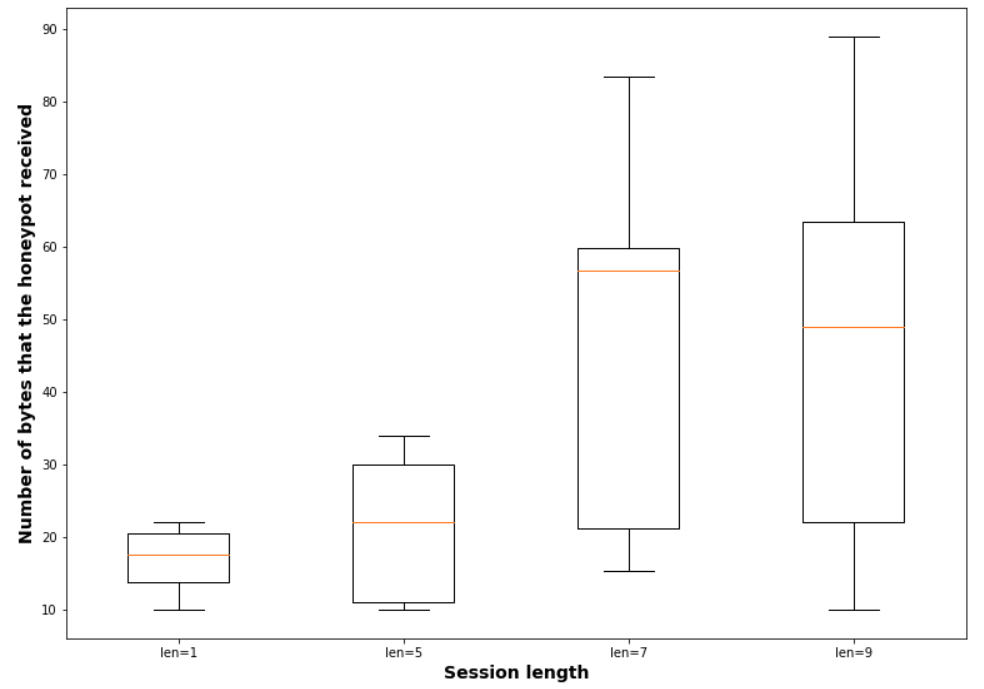
Figure 4: Volume of information that the honeypot receives per session length, illustrating the increase in attacker engagement data.
Conclusion
AIIPot represents a notable advancement in honeypot technology, leveraging machine learning to dynamically adapt IoT defenses to the ever-changing tactics of cyber attackers. By increasing interaction lengths and capturing a broader spectrum of attacks, AIIPot not only advances the state of honeypot design but also provides a framework for future development in intelligent security mechanisms for IoT networks. Future research will contemplate refining real-time model convergence and exploring resilience against model poisoning to enhance robustness in diverse deployment scenarios.





