- The paper introduces IceClave, a TEE for in-storage computing that secures SSD operations through ARM TrustZone-based memory partitioning.
- The methodology employs isolated memory regions, streamlined encryption, and an optimized FTL mapping table to balance security with performance.
- Performance evaluations reveal up to 2.31x speed improvements with only a 7.6% overhead, demonstrating its practical benefits for secure data processing.
IceClave: A Trusted Execution Environment for In-Storage Computing
The advancement of in-storage computing has enabled systems to offload computation-intensive tasks directly onto SSDs, thereby alleviating traditional I/O bottlenecks. The paper presents "IceClave: A Trusted Execution Environment for In-Storage Computing", a solution that addresses the security vulnerabilities associated with these architectures by introducing a secure, isolated execution environment for programs operating within SSDs.
Introduction and Architecture Overview
The core concept of IceClave is to implement a Trusted Execution Environment (TEE) tailored for SSD-based computing, emphasizing both security and performance. In conventional setups, SSD controllers lack support for trusted environments, which exposes them to risks such as data manipulation by malicious programs. IceClave leverages ARM's TrustZone technology to partition memory spaces into secure and normal worlds. This partitioning ensures that flash management tasks are protected from potential threats posed by untrusted programs.
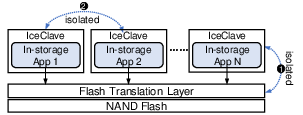
Figure 1: IceClave enables in-storage TEEs to achieve security isolation between in-storage programs, FTL, and flash chips. The shaded components are untrusted.
The architecture of IceClave incorporates unique memory regions, streamlined encryption mechanisms, and optimization strategies to minimize performance overhead while providing robust security.
Memory Protection and Isolation
An essential component of IceClave is the delineation of memory into distinct regions, as shown in the overview of its architecture. These regions include normal, protected, and secure memory spaces managed via TrustZone extensions (Figure 2).
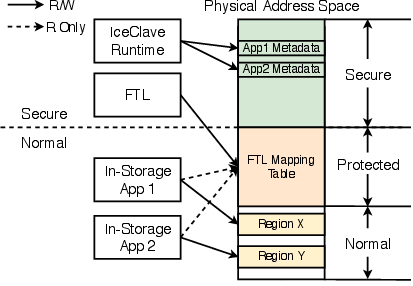
Figure 2: Memory protection regions in IceClave.
The protected memory area holds the FTL mapping table, enabling read-only access from the normal world to avert the high-cost context switches typically necessary for flash address translation. Figure 3 illustrates the performance gains from this optimization, demonstrating a marked improvement over configurations requiring secure world context switches for each access.
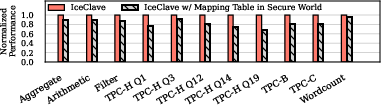
Figure 3: Performance comparison between IceClave and IceClave with FTL mapping table in secure world. Performance is normalized to IceClave.
Data Security and Encryption Techniques
IceClave institutes a lightweight stream cipher engine, bespoke for the SSD environment to encrypt/decrypt data transfers between storage processors and flash chips. The use of Trivium for this purpose maintains a low hardware footprint while ensuring data confidentiality (Figure 4).
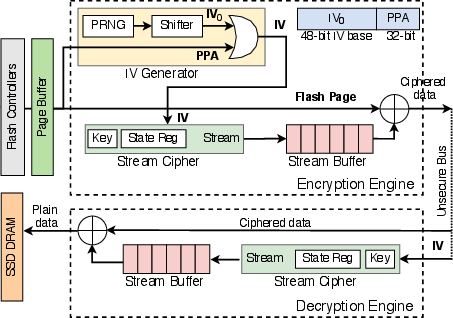
Figure 4: Stream cipher engine design in IceClave.
Additionally, the hybrid-counter scheme for memory encryption efficiently handles read-intensive workloads by using major counters for read-only pages, thereby optimizing performance and minimizing encryption-related overheads (Figure 5).
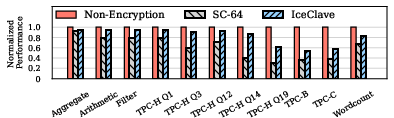
Figure 5: Performance comparison of Non-encryption, Split Counters (SC-64), and IceClave. It is normalized to the scheme without memory encryption.
IceClave was subject to rigorous performance tests using data-intensive applications such as those from the TPC-H benchmark suite. It was shown to deliver up to 2.31x performance improvements compared to conventional host-based computing despite incurring a nominal 7.6% overhead compared to insecure in-storage computing environments.
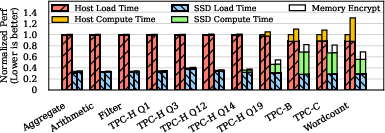
Figure 6: Performance comparison of Host, Host+SGX, ISC, and IceClave (from left to right). We show the performance breakdown of each scheme.
Implications and Future Directions
The introduction of IceClave represents a significant step forward in the field of secure in-storage computing. By offering robust security features with minimal overhead, IceClave facilitates the deployment of more secure, efficient SSD solutions capable of handling modern data center demands.
The paper suggests that future directions could explore further integration with emerging technologies such as RISC-V architectures and potential adaptations for use with in-storage hardware accelerators. These advancements could further enhance the scalability and applicability of IceClave in diverse operational environments.
Conclusion
In conclusion, IceClave adeptly balances the stringent demands of performance and security for in-storage computing. Its design demonstrates that efficient TEEs for SSDs can be achieved with strategic use of existing hardware capabilities and careful architectural planning. This work lays a foundation for increased adoption of SSDs in more critical roles within modern computational frameworks.







