- The paper presents a novel CLOPA methodology that integrates cyber risks into traditional LOPA for improved safety assessment in CPS.
- It introduces mathematical formulations linking protection layer reliability with cyber attack probabilities, enabling quantitative trade-off analysis.
- A process reactor case study demonstrates that ignoring cyber-induced failures can lead to significant under-design of safety systems.
Cyber LOPA: Integrating Safety and Security in Cyber-Physical System Design
Introduction
The paper "Cyber LOPA: An Integrated Approach for the Design of Dependable and Secure Cyber Physical Systems" (2006.00165) presents a rigorous methodology for the co-design of safety and security in Cyber-Physical Systems (CPS). The authors extend the classical Layer of Protection Analysis (LOPA) framework, widely used in industrial risk assessment, to incorporate failures induced by cyber attacks, resulting in the Cyber Layer Of Protection Analysis (CLOPA) formulation. The work addresses the quantitative interplay between reliability and security, providing a mathematical basis for integrated lifecycle engineering and demonstrating the approach on a process reactor case study.
Safety and Security Lifecycle Coupling
The IEC 61511 standard defines the safety lifecycle for Safety Instrumented Systems (SIS), emphasizing hazard identification, risk assessment, and allocation of safety functions to independent protection layers. Traditionally, risk assessment focuses on physical failures, assuming independence between layers. However, modern CPS architectures introduce cyber dependencies, particularly through networked communication between Basic Process Control Systems (BPCS) and SIS, violating the independence assumption.

Figure 1: IEC 61511 SIS design lifecycle, illustrating the stages from hazard identification to decommissioning.
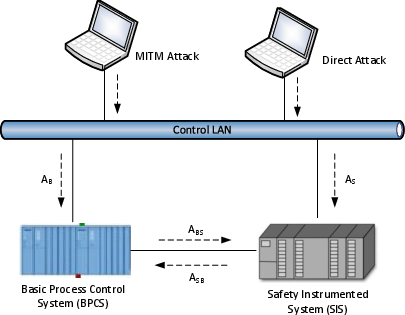
Figure 2: Industrial control system architecture showing BPCS-SIS connectivity and attack vectors, highlighting cyber dependencies.
The paper formalizes the joint failure probabilities arising from cyber attacks, distinguishing between direct attacks on SIS, pivot attacks via BPCS, and their impact on process hazards. The authors derive expressions for the probability of simultaneous BPCS and SIS security failures, accounting for attack vectors and their conditional dependencies.
CLOPA generalizes the LOPA calculation by introducing cyber-induced initiating events and their associated likelihoods. The expected number of hazardous events per unit time is expressed as:
E[H]=pλ
where p is the probability of simultaneous failure of all relevant protection layers, and λ is the expected rate of initiating events, now including cyber attacks. The formulation aggregates semantically-relevant attack events using weighted probabilities, enabling tractable risk assessment even with large attack trees.
The core CLOPA constraint is:
P[Sp]≤α1−α1P[Sc]+α2P[Bc]−α2P[Sc,Bc]β−(α1P[Sc]+α2P[Sc,Bc])
where P[Sp] is the SIS physical failure probability, P[Sc] and P[Bc] are SIS and BPCS security failure probabilities, and β, α1, α2 are functions of event likelihoods and protection layer reliabilities. This constraint quantifies the trade-off between reliability and security, directly linking SIS design requirements to cyber risk metrics.
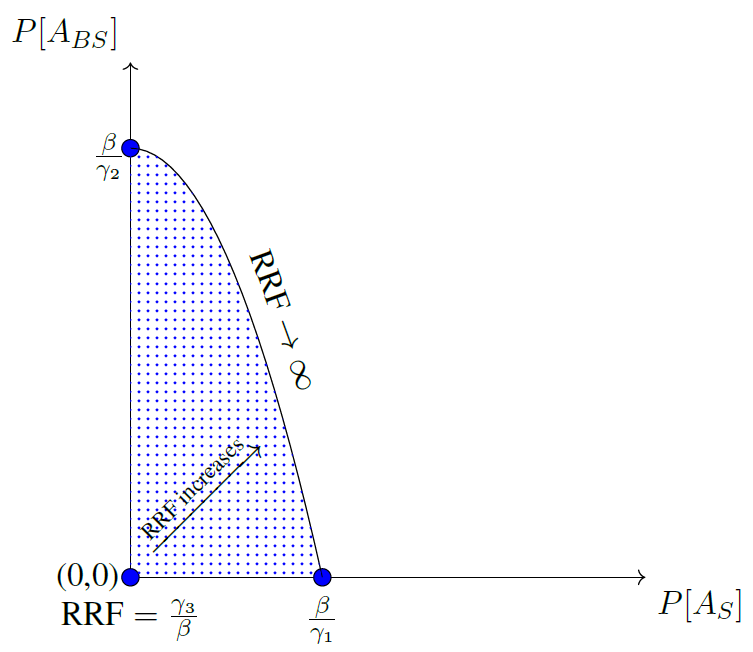
Figure 3: CLOPA Design Region (shaded). Feasible SIS designs lie within the region; boundary points require impractically high RRF values.
Integrated Safety-Security Lifecycle and Iterative Design
The authors propose an integrated lifecycle that couples safety and security risk assessment processes. The design proceeds iteratively: initial reliability and security targets are set, SIS architecture is developed, and both reliability (Risk Reduction Factor, RRF) and security failure probabilities are verified. If the CLOPA constraint is not satisfied, the design is refined, balancing fault tolerance and security hardening.
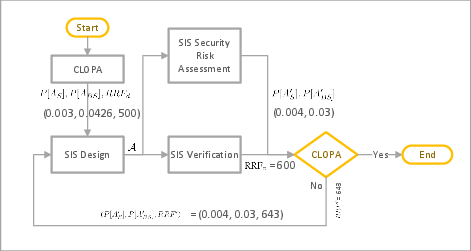
Figure 4: CLOPA Iterative Design Process, showing feedback between SIS design, verification, and risk assessment.
This approach is operationalized via an algorithmic workflow, enabling practical implementation in industrial settings. The lifecycle ensures that safety and security requirements are not treated in isolation, but as interdependent constraints.
Case Study: Process Reactor System
A detailed case study on a Continuous Stirred Tank Reactor (CSTR) demonstrates the CLOPA methodology. The system comprises a BPCS and SIS, with networked communication following NIST 800-82 guidelines.
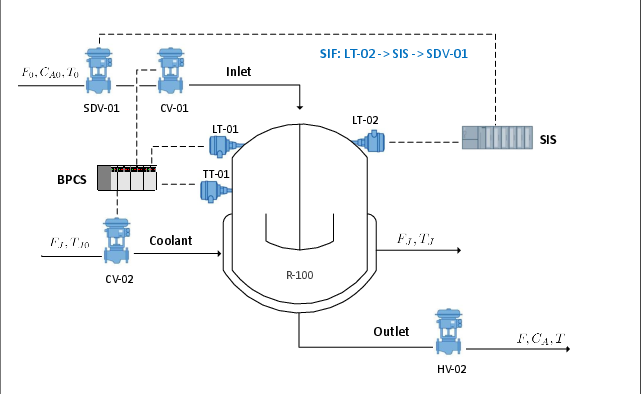
Figure 5: Reactor Piping and Instrumentation Diagram (P&ID) for the CSTR process.
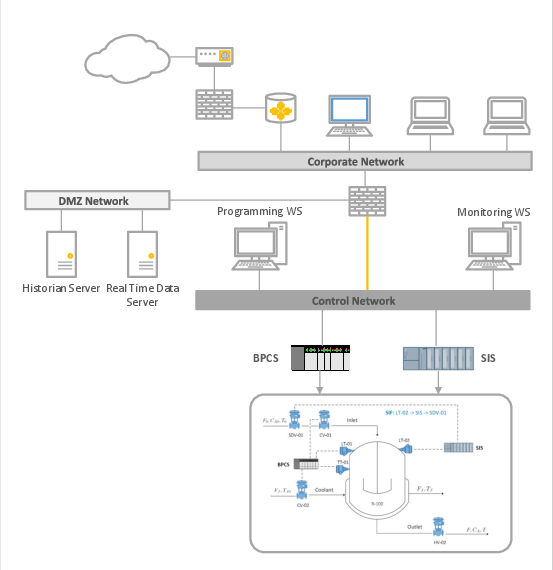
Figure 6: CPS architecture for the industrial control system testbed, enforcing network segmentation and DMZ access controls.
The authors conduct HAZOP analysis to identify hazards, enumerate initiating events (including cyber attacks), and construct attack trees for BPCS and SIS compromise. Probabilities for attack success are estimated via penetration testing and vulnerability analysis. The CLOPA constraint is instantiated with real system parameters, and the design region is visualized, guiding selection of feasible SIS architectures.
Strong numerical results are reported: for the case study, classical LOPA yields RRF = 113, while CLOPA (accounting for cyber risk) requires RRF ≥ 117 for a perfectly secured SIS, and RRF ≥ 500 for realistic attack probabilities. The error induced by ignoring cyber failures is quantified, reaching eRRF=378 for typical design points—demonstrating that classical LOPA can significantly under-design protective systems.
Sensitivity and Practical Implications
The sensitivity analysis reveals that CLOPA is more responsive to direct SIS attack probabilities than to pivot attacks via BPCS. The model is robust for small probability variations, but becomes highly sensitive near the design boundary, where small changes in cyber risk can necessitate large increases in RRF. This underscores the importance of conservative design and accurate cyber risk quantification.
The integrated lifecycle and CLOPA formulation have direct implications for industrial practice. They enable systematic co-design of safety and security, support quantitative trade-off analysis, and can be embedded in model-based engineering toolchains. The approach is compatible with existing standards (IEC 61511, NIST SP 800-30) and can be extended to joint optimization of BPCS and SIS architectures.
Theoretical and Future Directions
The work advances the theoretical understanding of safety-security interactions in CPS, providing a formal basis for lifecycle integration and risk assessment. It highlights the necessity of treating cyber failures as first-class hazards in safety engineering. Future research directions include:
- Joint optimization of control and safety system architectures under combined safety-security constraints.
- Development of automated toolchains for CLOPA-based design and verification.
- Extension of the framework to other domains (e.g., medical devices, transportation, energy systems).
- Investigation of the reverse interaction: how safety failures can induce or amplify security risks.
Conclusion
The CLOPA methodology rigorously integrates cyber risk into safety assessment for CPS, quantitatively demonstrating that neglecting security failures can result in substantial under-design of protective systems. The iterative, integrated lifecycle enables practical co-design of reliability and security, with strong numerical evidence supporting the necessity of this approach. The framework is extensible, compatible with industrial standards, and provides a foundation for future research in dependable and secure CPS engineering.







