- The paper presents a sliding mode observer (SMO) that robustly detects and estimates cyber-attacks on autonomous vehicle platoons.
- It employs event-triggered communication with adaptive OSA and MSA thresholds to mitigate false alarms while ensuring accurate detection.
- Simulations under continuous and event-triggered scenarios validate the method's resilience against measurement uncertainties and communication delays.
Sliding Mode Observer for Attack Detection in Autonomous Vehicle Platoons
Introduction
The research paper presents a robust method for detecting and estimating cyber-attacks on platoons of autonomous vehicles using a sliding mode observer (SMO) in the context of event-triggered communication within Cooperative Adaptive Cruise Control (CACC) systems. The work specifically addresses the vulnerabilities in Vehicle-to-Vehicle (V2V) communication protocols by providing stability proofs for the observer in a realistically challenged environment with communication-triggered events and measurement uncertainties.
The authors formulate the problem by first modeling the dynamics of a vehicle platoon under CACC. This includes the mathematical description of vehicle error dynamics in the presence of noise and potential cyber-attacks, which are expressed as state-space models. The attack is conceptualized as a man-in-the-middle attack on the communicated acceleration between vehicles.
Sliding Mode Observer Design
The implementation of the SMO is central to this paper. The observer incorporates both continuously updated and event-driven elements to ensure robustness in a V2V context. This design separates the measured and unknown states to control the sliding of states along ϵy,i(t)=0. The observer error dynamics are carefully articulated to establish bounds on estimation errors while maintaining robustness against measurement uncertainties and attacks.
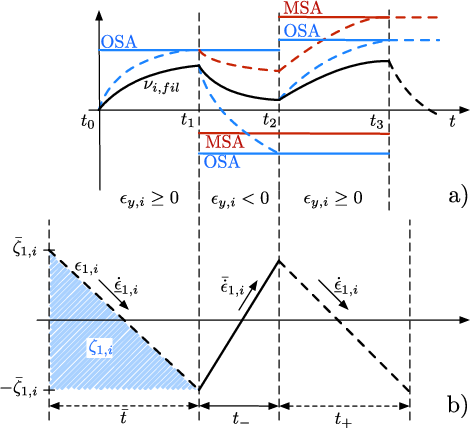
Figure 1: A graphical illustration of the OSA and MSA threshold computations for the first three switching periods of the SMO.
Robust Detection Thresholds
Two attack detection thresholds—One-Switch-Ahead (OSA) and Multiple-Switches-Ahead (MSA)—are developed to avoid false alarms without sacrificing detection capability. The OSA threshold quickly detects abrupt changes in system behavior potentially indicating attacks. Conversely, the MSA threshold considers longer time spans and switching behavior, promoting resilience against noise and communication delays.
Simulation Scenarios
Two simulation scenarios, continuous and event-triggered communication, demonstrate the SMO's effectiveness. The former shows prompt response without false positives, while the latter showcases the adaptability of the methodology to event-triggered frameworks. Alert thresholds are recalculated at communication triggers to adapt to asynchronous updates effectively.
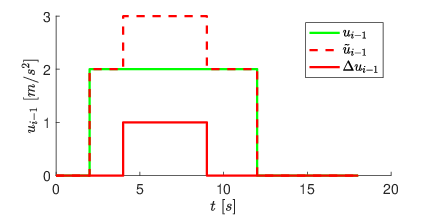
Figure 2: Simulation Scenario for attack on communication between car 1 and 2.
Attack Estimation
An extension of the observer mechanism is applied to quantify the impact of detected attacks by extrapolating the fault-induced variances in the SMO's output. These results, although preliminarily assessed in simulations, indicate the capability of the observer, even under non-ideal conditions, to approximate attack characteristics with a reasonable accuracy.
Conclusion
The work concludes by proposing a methodologically sound and computationally feasible solution to the issue of cyber-attack detection and estimation in autonomous vehicle platoons. Future research is directed toward refining these estimates under more general conditions and integrating them into broader non-linear models. The adaptive thresholds reinforce the method's resilience to environmental disturbances and communication inconsistencies, making it a viable tool for real-world deployment.
The paper's contribution to cyber-physical system security particularly in intelligent transportation systems highlights the importance of advanced observer designs which can be potentially expanded to various other application domains within networked control systems. The SMO design and its associated thresholds are critical to assure reliable operation of autonomous vehicle networks against sophisticated cyber threats.



