- The paper introduces a hierarchical threat model evaluating remote, network, and physical attack vectors affecting imaging devices.
- It employs an empirical assessment of 15 devices to reveal encryption gaps and suboptimal update practices.
- The study recommends robust measures like encrypted data transmission, node authentication, and system hardening to enhance device security.
Security of Medical Cyber-Physical Systems: An Empirical Study on Imaging Devices
Medical cyber-physical systems are increasingly being integrated into hospital networks, with imaging devices playing a crucial role. This paper investigates the security issues surrounding these systems, focusing primarily on imaging devices. The study introduces a threat model, potential attack vectors, and protective mechanisms while evaluating their effectiveness.
Threat Model and Attack Techniques
Attack Vectors
The research outlines three primary attack vectors:
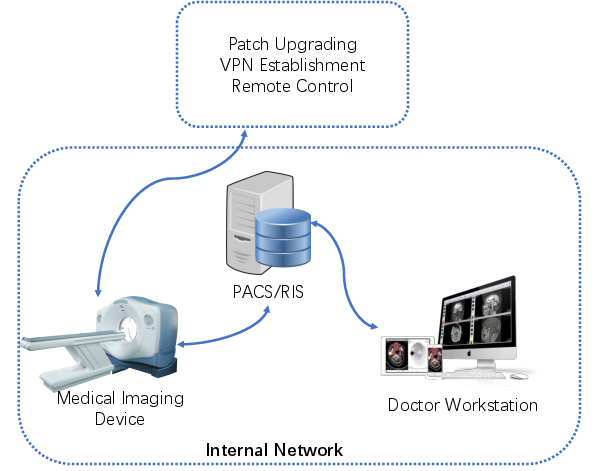
- Remote Server Poisoning: Imaging devices often connect to vendors' servers for tasks such as patch upgrades and remote control. If these servers are compromised, attackers can propagate malware and hijack network traffic.
- Internal Network Penetration: Hospitals frequently provide public WiFi access, making internal networks susceptible to attacks such as ARP spoofing and social engineering that target imaging devices.
- Physical Brute Force: Physical access to devices can allow attackers to directly extract sensitive data, highlighting the need for robust physical safeguards.
Techniques
Different attack techniques include port scanning, traffic analysis, and reverse engineering:
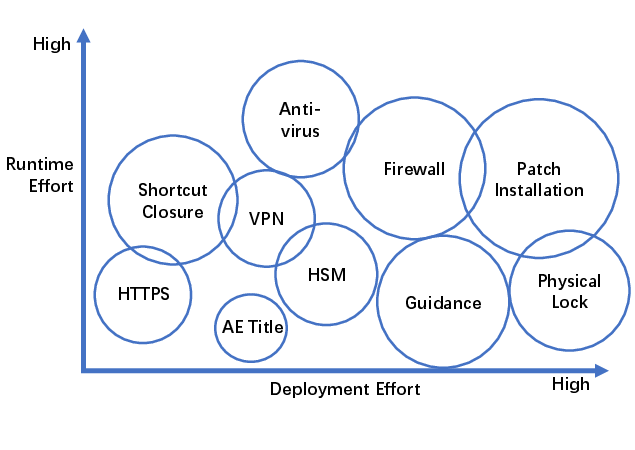
Protection Mechanisms
The paper thoroughly evaluates various protection mechanisms:
Network and System Safeguards
Hierarchical Security System
To aid in evaluating device security, the paper proposes a hierarchical system, categorizing devices based on their protection level (e.g., CL1, CL2, CL3) with various safeguards' implementations. Higher levels require comprehensive features like full encryption and advanced identity authentication.
Empirical Evaluation
The study assesses 15 medical devices, revealing significant gaps in encryption, auditing, and update practices across manufacturers. Some devices default to the minimal security configurations without meeting advanced requirements.
Conclusion
This empirical evaluation underscores the urgent need for improved security in medical cyber-physical systems, especially imaging devices. It introduces a structured hierarchical security assessment model, encouraging both vendors and regulatory bodies to adopt robust protection strategies for safeguarding sensitive healthcare data. Future research should explore innovative solutions for improving node authentication and system hardening practices.